Use BGP attributes to solve the requested action…
exhibit LAB 5
Company Acan has two links which can take it to the Internet. The company policy demands that you use web traffic to be forwarded only to Frame Relay link and other traffic can go through any links that are available. Use BGP attributes to solve the requested action.
Answer and Explanation:
All the HTTP traffic from the Server should go through Frame Relay link and all the other traffic should go through EoMPLS link.
The only router you are able to administrate is the Border Router, from the server you may only send HTTP traffic. As the other people mentioned, actually it is not a BGP lab. You are not able to execute the command "router bgp 65001"
For the solution I did the following:
1) Access list that catches the HTTP traffic:
access-list 101 permit tcp any any eq www
Note that the server was not directly connected to the Border Router. There were a lot of EIGRP routes on it. You do not know the exact IP address of the server, so the ACL catches all the source addresses.
2) Route map that sets the next hop address to be ISP1 and permits the rest of the traffic:
route-map pbr permit 10
match ip address 101
set ip next-hop 10.1.101.1
route-map pbr permit 20
3) Apply the route-map on the interface to the server:
int fa0/0
ip policy route-map pbr
When you send traffic from the server the route map should match, you may check with:
show route-map
LAB
Company Acan has two links which can take it to the Internet. The company policy demands that you use web traffic to be forwarded only to Frame Relay link and other traffic can go through any links that are available. Use BGP attributes to solve the requested action.
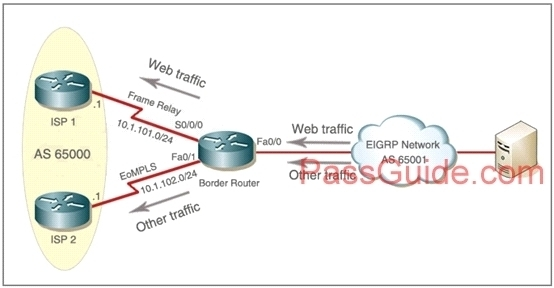
Answer and Explanation:
All the HTTP traffic from the Server should go through Frame Relay link and all the other traffic should go through EoMPLS link.
The only router you are able to administrate is the Border Router, from the server you may only send HTTP traffic. As the other people mentioned, actually it is not a BGP lab. You are not able to execute the command “router bgp 65001”
For the solution I did the following:
1) Access list that catches the HTTP traffic:
access-list 101 permit tcp any any eq www
Note that the server was not directly connected to the Border Router. There were a lot of EIGRP routes on it. You do not know the exact IP address of the server, so the ACL catches all the source addresses.
2) Route map that sets the next hop address to be ISP1 and permits the rest of the traffic:
route-map pbr permit 10
match ip address 101
set ip next-hop 10.1.101.1
route-map pbr permit 20
3) Apply the route-map on the interface to the server:
int fa0/0
ip policy route-map pbr
When you send traffic from the server the route map should match, you may check with:
show route-map
